Trojan Backdoor – Trojan Attack Methodology And How to Detect and Prevent Trojan Attacks
“A Trojan Backdoor is a malicious software which is often, hidden behind a software or a file
which look legitimate and execute itself in the background, and open a backdoor for the threat actors to
gain elevated access of the victim machine”
Hey Fellas,
With the advancement of computer systems, there is a proportional increase in cybercrimes. Cyber criminals are continuously reconnoitering IT systems to find vulnerabilities and ways to exploit them. Since inception, one of the most powerful tools used by threat actors to gain control over the victim system is by installing a Trojan backdoor software through various methods. In this article, we will be discussing the different types of trojan backdoors, their attack methodology, and the way to protect the IT systems from Trojan backdoors.
Backdoors represent software or hardware components integrated into IT systems. They offer manufacturers and threat actors means to attain administrative access to these systems, either for lawful intentions or to execute malicious operations. Often, these backdoors serve as conduits for cybercriminals to secure administrative control over targeted systems. In certain instances, manufacturers intentionally design backdoors to oversee system activities for analysis and facilitate maintenance tasks. It’s important to acknowledge that backdoors may inadvertently find their way into systems during programming or manufacturing, owing to suboptimal coding practices and inadequate security testing.
Two primary types of backdoors exist:
- Hardware Backdoor
- Software Backdoor
Hardware Backdoor
These backdoors are typically crafted by original equipment manufacturers (OEMs) for legitimate purposes, such as recovering lost passwords through administrative access. These backdoors find their residence within hardware chips, taking the form of code and interfacing with the actual circuitry. Another approach involves introducing modified circuits that trigger payload delivery modules under specific conditions. These methods are also identified as hardware trojans, serving as a direct means to attain elevated access to the system. If attackers manage to uncover the entry points to these backdoors, they can easily exploit and reverse-engineer them, employing them for malicious activities on targeted systems. As a result, these backdoors are typically held in utmost confidentiality by the OEMs.
Software Backdoor
A backdoor is not classified as a trojan until it’s integrated into legitimate software and the backdoor payload is surreptitiously delivered, avoiding user detection. Hence, a Trojan Horse Backdoor, or more simply, a Trojan Backdoor, is a lightweight software component merged with genuine software and discreetly transported to the target device through diverse methods, such as phishing emails.
These lightweight trojan backdoors are meticulously engineered to grant attackers administrative control. By exploiting these backdoors, attackers can proceed to install more intricate malicious software, capable of inflicting greater catastrophic harm to the target system and its data.
Once attackers attain administrative control, they can traverse the system horizontally, elevate privileges, establish enduring backdoor access through rootkits, capture user credentials through keyloggers, and amass personal and financial data. They can deploy ransomware, and even irreversibly impair the target system by manipulating hardware component parameters.
In essence, a trojan horse backdoor imperils Confidentiality, Integrity, and Availability simultaneously. These attacks are among the most infamous, enabling attackers to amplify their assault from mere reconnaissance to complete system incapacitation or the exfiltration of entire data repositories. Attackers can also exploit victim systems as launching points to infect other network systems, compromising the entire network’s security.
Trojan Horse
Based on the purpose and usage, trojan horses are classified into below types.
- Trojan Backdoor
- Banking Trojan
- DDOS Trojan
- Fake Antivirus Trojan
- Trojan – GameThief
- Trojan IM (Instant messaging)
- Trojan-Ransom
- SMS Trojan
- Trojan Spy
- Trojan – Mailfinder
While trojan horses can be categorized into the aforementioned groups, a trojan backdoor possesses inherent autonomy to execute all the aforementioned operations. Upon successfully deploying a trojan backdoor, the attacker gains comprehensive authority to install any of the previously mentioned trojans and execute intricate assaults on the targeted system. This section will delve into an in-depth exploration of the trojan backdoor.
Tools and Software Used by Attackers to Create Trojan Payloads
A trojan backdoor’s code can be scripted in various languages, depending on the runtime environment of the targeted machine. Attackers commonly employ reconnaissance and social engineering techniques to gather information about the target IT infrastructure, such as the operating system, underlying hardware, installed services, user data, IP addresses, and router details. Armed with this knowledge, they can opt to craft personalized trojan backdoors or utilize readily available software designed for generating pre-made trojan backdoor scripts.
To enable the functionality of a trojan backdoor, two key software components are required:
- Trojan backdoor server: This component, reserved by the attacker, maintains continuous vigilance over incoming connections from clients (victim machines). Once a connection is established, the attacker can dispatch malicious instructions via this server to the victim machine. Usually referred as Command and Control center.
- Trojan backdoor client: Termed as the payload, this component is deployed into the victim machine to establish a reverse connection with the trojan backdoor server.
Several off-the-shelf software tools capable of producing the aforementioned trojan backdoor components are as follows:
- Msfvenom
- njRAT
- fatRAT
- proRAT
For crafting trojan backdoor components targeting Android devices, tools such as the following can be employed:
- EvilDroid
It’s essential to note that these software options tend to be effective when the targeted machine lacks updated security patches, operates without antivirus protection, or has its firewall disabled. However, more recent versions of defenders and firewalls may already detect trojans generated through these tools. Therefore, for heightened attack effectiveness, attackers often resort to scripting their own customized backdoor code in languages like Ruby or Python and leverage tools like ‘Wine’ to generate executable files.
Tools and Software Used by Attackers to Obfuscate the Payload
Once the client executable file is generated, attackers do not simply transmit it to the target. Instead, they encode and blend it with legitimate software code, rendering them impervious to detection by both antivirus software and the targets themselves. Below are several tools crucial to accomplishing this objective, commonly referred to as packers:
- iexpress
- Ultimate Packer for Executables (UPX)
- The Enigma Protector
- MPRESS
- Exe Packer 2.300
- ExeStealth
- Morphine
- Themida
- MEW
- FSG
- PESpin
- Andromeda
- VMProtect
- Obsidium
These tools, often categorized as packers, play a pivotal role in camouflaging the malicious payload within the legitimate software, enhancing its chances of evading detection.
Trojan Droppers
These tools operate as conveyance mechanisms for disseminating the payload. Often, this software presents itself as authentic and occasionally valuable to users. However, beneath this façade lies encoded and altered trojan executable code. Instances of such software include Keygen programs and full version cracks. Typically, users are prompted to disable their system defenses to enable the functionality of these programs. Upon disabling these defenses and executing these applications, they carry out their intended functions while surreptitiously deploying trojan backdoor code to victim machines in the background, unbeknownst to the user. Notable examples of Trojan Droppers encompass:
- Keygen programs
- Software cracks
- Game cracks
- Illegitimate software patches
These Trojan Droppers operate under the guise of legitimate utility while surreptitiously facilitating the introduction of malicious code, leveraging the unsuspecting user’s cooperation in disabling security measures.
Trojan Downloaders
These mechanisms function akin to trojan droppers, with the sole distinction being that they do not harbor the trojan backdoor executable within themselves. Instead, they house a streamlined code designed to establish a connection to an external server at a later point, facilitating the download and installation of the actual trojan client executable. The channels employed for these operations align with those of Trojan Droppers. Trojan Downloaders can even camouflage themselves as authentic programs, including well-known applications like Windows Calculator or Notepad, designed to appear highly credible while harboring modified, packed code.
These Trojan Downloaders share parallels with trojan droppers in operation but differ in their approach of delivering the actual trojan client executable via an external server connection, often employing seemingly legitimate programs as disguises to enhance their camouflage.
Rootkits
Analogous to door stoppers, rootkits fulfill the role of securing the attacker-created backdoor, ensuring it remains accessible whenever necessary. Rootkits duplicate the trojan backdoor code, enabling them to reinstate the malicious service even in cases where it’s halted. In trojan backdoor attacks, rootkits find extensive application, often being implanted onto victim machines by attackers subsequent to obtaining administrative control over them. Rootkits serve as a pivotal element for preserving unauthorized access and control over compromised systems.
Trojan Backdoor System
A conventional firewall functions by scrutinizing incoming connections to the system. However, a trojan backdoor program establishes a reverse connection from the victim machine to the attacker’s server. Consequently, the firewall typically permits this traffic to traverse, as it constitutes an outbound connection originating from the machine itself. Below figure provides a visual representation of this operational pattern.
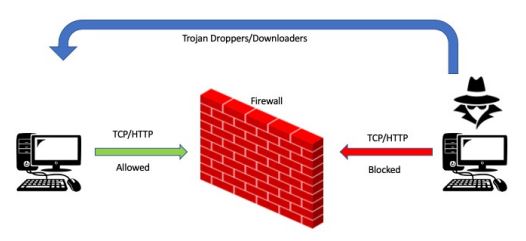
Trojan Attack Methodology
Trojan backdoor programs are meticulously tailored for distinct target sets. The program devised for one set might lack efficacy for another. Consequently, such attacks demand a high degree of precision. Prior to launching an assault on the target system, substantial effort is dedicated to comprehensively studying the system itself. This encompasses its attributes, operational features, active services, and critical functions. The trojan backdoor code is subsequently adapted to suit the specific information gleaned.
Phase 1:
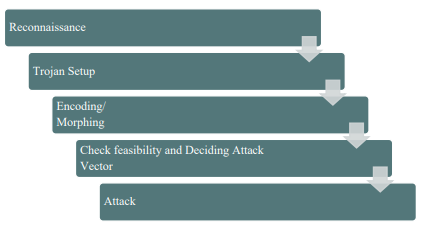
Phase 2:

Step 1: Reconnaissance
Prior to launching trojan attacks, a thorough understanding of the target infrastructure is paramount. Since executable files are OS-specific, such as an executable designed for Windows being incompatible with Linux systems, reconnaissance is crucial. Attackers leverage scanning tools like Nmap or Zenmap to glean insights about the target’s IP address, discerning its OS and overall infrastructure. Additionally, attackers may employ social engineering techniques to gather pertinent information about the target system.
Step 2: Payload, Command and Control Setup
Subsequently, attackers embark on constructing the trojan backdoor server and payload, meticulously tailored for deployment on the intended victim machine. Attackers may choose to utilize existing tools available on the dark web for crafting the server and payload, or they may opt to employ personalized code, as elucidated in the preceding section.
Step 3: Obfuscating the Payload
To ensure successful infiltration, the payload is encoded through cryptographic algorithms and paired with trojan droppers or downloader programs. Care is taken to initiate the decryption algorithm only after successful infiltration by the dropper/downloader. Automation scripts are employed to amalgamate specific segments of the trojan code post-infiltration.
Step 4: Check Feasibility and Decide Attack Vector
Attackers assess the feasibility of the trojan code through multiple antivirus scans. Tools like “http://www.antiscan.me/” may be employed to evaluate whether antivirus software detects the trojan within the dropper program. In instances where most antivirus software detects the trojan, the attacker revisits the code and introduces necessary modifications to evade detection. Depending on the reconnaissance data, the attacker determines the most suitable attack vector. This vector could include tactics like phishing emails or websites containing seemingly legitimate software cracks, patches, or enticing free content.
Step 5: Attack
The attacker inserts the trojan malware dropper/downloader into the chosen attack vector and awaits the target user’s interaction. When the target user downloads and runs the malware, a backdoor is created, establishing a connection with the attacker’s server. This connection grants the attacker administrative privileges on the victim machine. Notably, the victim remains oblivious to the backdoor’s existence, as the installation transpires discreetly in the background, devoid of any visible pop-ups or command terminals.
Step 6: Install Rootkit
Having infiltrated the victim machine, the attacker progresses to the second phase of the attack. With administrative privileges secured, the attacker proceeds to install supplementary malware. The initial preference typically leans towards installing a rootkit. This rootkit enables the attacker to sustain backdoor access, even if the malicious backdoor service is interrupted. The rootkit ensures the service’s restart and facilitates reconnection with the attacker’s server.
Step 7: Install Other Malicious Software
In addition to the rootkit, the attacker deploys additional tools and services necessary to achieve the attack’s ultimate objectives. These objectives might encompass a range of activities, from pilfering system and user data, system logs, licenses, and cryptographic keys, to executing keylogging, downloading storage or database contents, and extracting user credentials. Alternatively, the attack might involve vulnerability scanning, identifying systems with open ports and vulnerabilities, or even causing data loss in the victim system.
Step 8: Achieve Attack Goals
With the deployment of malicious tools and software, the attacker advances to realizing their objectives on the victim machine. The backdoor offers a diverse array of opportunities for system exploitation, yielding a broad spectrum of potential outcomes. Attack objectives span from data theft and system manipulation to reconnaissance of vulnerabilities across the network.
Step 9: End the Attack and Cover Tracks
Upon achieving all goals, the attacker might invest time to evade detection by sophisticated antivirus programs. Once their objectives are fulfilled, the attacker proceeds to conceal their tracks and discreetly exits the compromised system. Actions undertaken include erasing suspicious logs, revoking temporary accesses, uninstalling utilized malicious software, eliminating the rootkit, and disengaging from the target system. Notably, unless the attack seeks to compromise data integrity, the attacker often avoids conspicuous file and folder modifications, rendering their exit virtually undetectable on the victim machine.
Trojan Detection
Just like any other malwares, trojan backdoors can be detected and mechanisms are available to
prevent trojans from infiltrating the IT systems.
Employing EDR (Endpoint Detection and Response) Software
Endpoint Detection and Response (EDR) software is a cybersecurity solution designed to safeguard computer systems by continuously monitoring and analyzing endpoint activities. EDR provides real-time threat detection, incident response, and forensic investigation capabilities, enabling swift identification of potential security breaches. Through advanced techniques like behavior analysis and machine learning, EDR solutions offer enhanced visibility into endpoint behavior, aiding in the detection of sophisticated threats that might evade traditional security measures. By allowing security teams to respond rapidly and effectively to potential threats, EDR plays a critical role in minimizing the impact of security incidents on an organization’s digital infrastructure. A wide variety of EDR solutions are available in the market which can detect the malicious software based on the IOCs ( Indicators of compromise) and hash values specific to the malicious software.
Port Scanning
System administrators must be well-versed in the requisite open ports required for user-assigned tasks. Adversaries can exploit any extraneous open ports by establishing reverse connections via trojan backdoors. In case of suspected trojan infections, the initial step entails disconnecting from the internet and conducting a port scan using tools such as Nmap, Netcat, Angry IP Scanner, Unicornscan, and others. These scan results unveil any undesired open ports within the system.
System Behavior Analysis
While traditional PCs exhibit noticeable signs like diminished system performance and sluggishness in the event of a trojan infection, such indicators might not be as apparent in auto-scalable systems. Consequently, continual monitoring and alerts derived from system log files become pivotal. Tools like Splunk, Logstash, Kibana, and Papertrail prove invaluable in pinpointing and notifying instances of open and unauthorized ports attempting communication with the external environment.
Network Scanning and using SIEM Tools to Detect Unknown External Connection
Utilizing tools like Wireshark, segments of network traffic can be scrutinized to identify target hosts with which the system communicates. Any unanticipated TCP or HTTP communication with unfamiliar hosts can be detected and subsequently blocked using firewalls, thereby curbing unauthorized data flow.
Additionally, most of the SIEM (Security Information and Event Management) solutions in the market are capable of streaming the network log and detecting any unknown external connection made by any internal systems. It is always a best practice to have a SIEM solution in place which continuously monitors the IT infra.
Use Advanced Antivirus Software with Updated Database
A majority of antivirus software incorporate trojan detection systems. These antivirus programs dynamically recognize files that share signatures with trojan viruses. Upon detection, these programs promptly identify and eliminate the malicious software or file from the system, acting as a safeguard against trojan infiltrations.
Trojan Prevention
| Attack Vector | Defense Mechanism |
|---|---|
| Phishing Email | 1) Mandatory Security Training to users. 2) Security awareness assessments. 3) Conducting Phishing simulations. 4) Blocking email from unknown domains. 5) Downloadable content blocked by default. 6) Using antivirus software with email security. |
| Weak/Stolen Credentials | 1) Setting password policies. 2) Do not allow short passwords. Set minimum password length. 3) Set password complexity level to high. 4) Change the default passwords. 5) Do not write/share the password anywhere/with anyone. |
| Malicious Insider | 1) Deploy zero trust strategies wherever required. 2) No access must be given to users by default. 3) Unnecessary access must be diligently audited and revoked. User must request for the access again based on the need. 4) All programs developed or security changes must be peer reviewed and go through change management process. |
| Misconfiguration | 1) Unused ports must be closed. 2) Restrict access to confidential folders. 3) Monitor and Audit configurations continuously. 4) Configure firewall, inbound and outbound rules vigilantly. 5) Use vulnerability assessment tools to detect configurations which could lead to trojan attacks |
| Storage Devices | 1) Use an updated antivirus software. 2) Block hardware ports like USB from mounting storage devices. 3) Block Disk drivers from reading a CD/DVD. 4) Lock the system boxes physically, to make sure none gets access to the internal ports and storage devices. 5) Schedule automated antivirus scans for all files on the storage devices. 6) Encrypt the files on storage devices. |
| Web Applications | 1) Block any non SSL web application. 2) Block API calls from unknown applications. 3) All authorized web applications must undergo security assessment before being deployed. 4) Scan the source code for possible trojan backdoors. 5) Block malicious application calls from unknown sources using firewalls. |
| Software Upgrades/Patches | 1) Do not trust any patch/update available for download. 2) Always compare the hash given by the OEM with the hash of the program which you downloaded. They both must match. 3) Scan the executables and shells using antivirus software to detect any encryption of malware or any malicious code. 4) Scan the patches and upgrade files for trojan downloaders which make external calls to download the trojan. |
| Network | 1) Isolate internet facing applications from backend infrastructure using VPN architecture. 2) Implement Firewalls at different layers of the infrastructure. 3) Monitor network traffic continuously for any unknown external connections. |
Trojan backdoors pose significant danger due to their capacity to attain administrative privileges, directly endangering data confidentiality, integrity, and availability within victim systems. When signs of trojan detection emerge, the initial response involves disconnecting from the internet. By severing the internet connection, the efficacy of backdoors is nullified. This preemptive measure is crucial, preventing adversaries from employing automated scripts through the backdoor post-detection.
Subsequent steps involve safeguarding against further compromise. This entails backing up critical files, formatting the system, reinstalling the operating system, and then restoring the files. Thorough scans are imperative to ensure the absence of any residual trojan traces.
User vigilance is paramount when navigating the internet, downloading content from emails, and interacting with unfamiliar links. These actions are primary entry points for trojan backdoors, underscoring the need for cautious online behavior.
Please state your views, questions or suggestions in the comments section.
Happy Learning !
